Every breakthrough in identity verification creates new possibilities. Every advancement in fraud techniques creates new vulnerabilities Now the challenge isn’t just choosing the right technology. It’s understanding how these technologies actually work, where they succeed, where they fail, and how attackers are learning to exploit them.
Facia delivers the technical intelligence, performance benchmarks, and implementation insights that help organisations navigate the rapidly evolving biometric landscape.
The same AI that powers facial recognition also generates deepfakes. The same neural networks that detect fraud also help fraudsters bypass detection. Technology doesn’t just solve the identity problem, it constantly reshapes it.
Use facial recognition for authentication globally in 2025
Exploit static images or video replays to bypass biometric systems
Report deepfakes as a growing threat to enterprise integrity
In synthetic identity fraud cases between 2021-2023
Organisations implementing biometric identity systems face fundamental questions that vendor marketing rarely addresses:
More accurate systems often require more data collection—how do you balance effectiveness with user rights and regulatory compliance?
Faster verification improves user experience but may miss sophisticated attacks—where’s the acceptable tradeoff?
Systems optimised for specific demographics may fail for others—how do you ensure equitable performance?
New detection methods emerge alongside new attack techniques—how do you stay ahead of the curve?
Initial implementation is straightforward; adapting to emerging threats requires continuous evolution—are you prepared?

Over 1.4 Billion Devices will use facial recognition for authentication in 2025
92% of Deepfake Attacks exploit static images or video replays
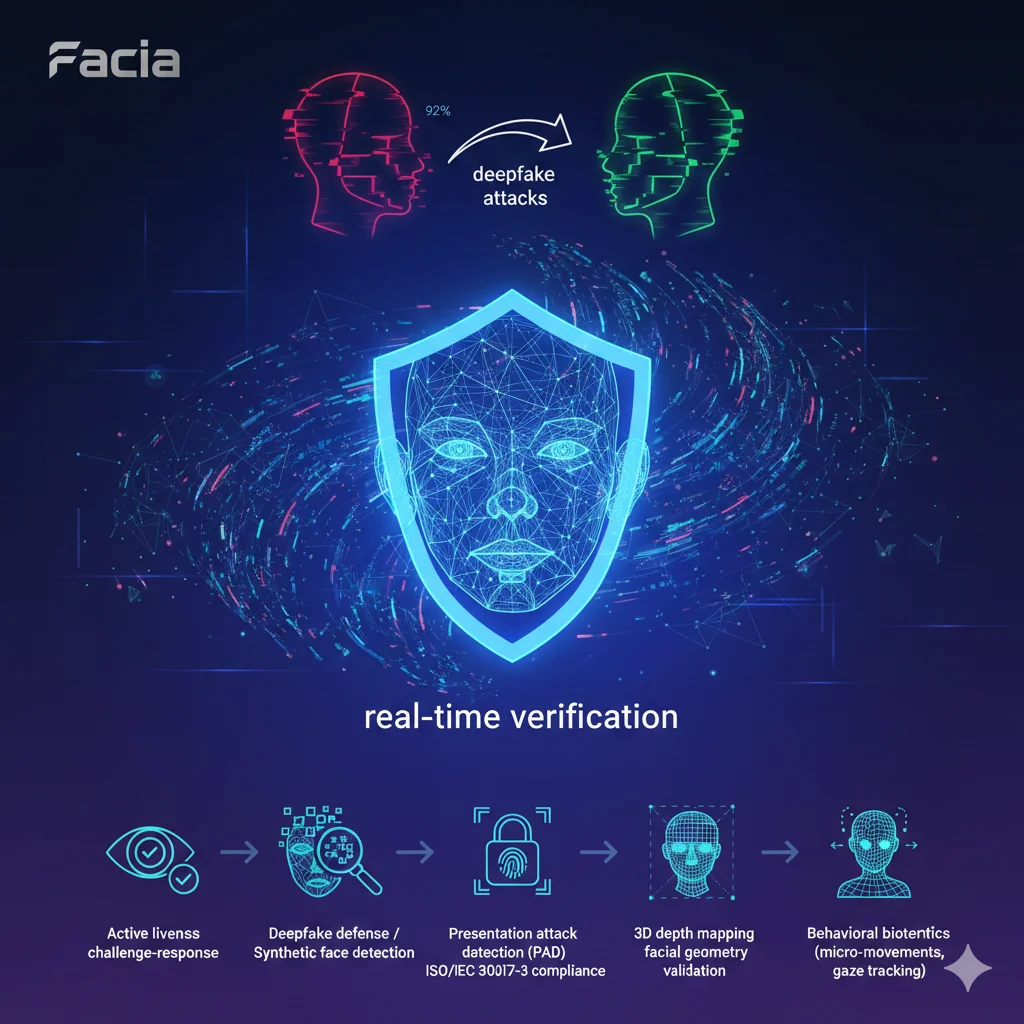

66% of Organizations report deepfakes as a growing threat to enterprise integrity
We analyze emerging biometric threats, fraud pattern evolution, and regulatory developments across industries and geographies.

We provide comprehensive guides, implementation frameworks, and compliance mapping that demystify complex identity verification.

We give you the knowledge to evaluate solutions, assess risks, and build strategies independently without vendor pressure.
Implementing biometric technologies without deep understanding creates risks that extend far beyond initial deployment:




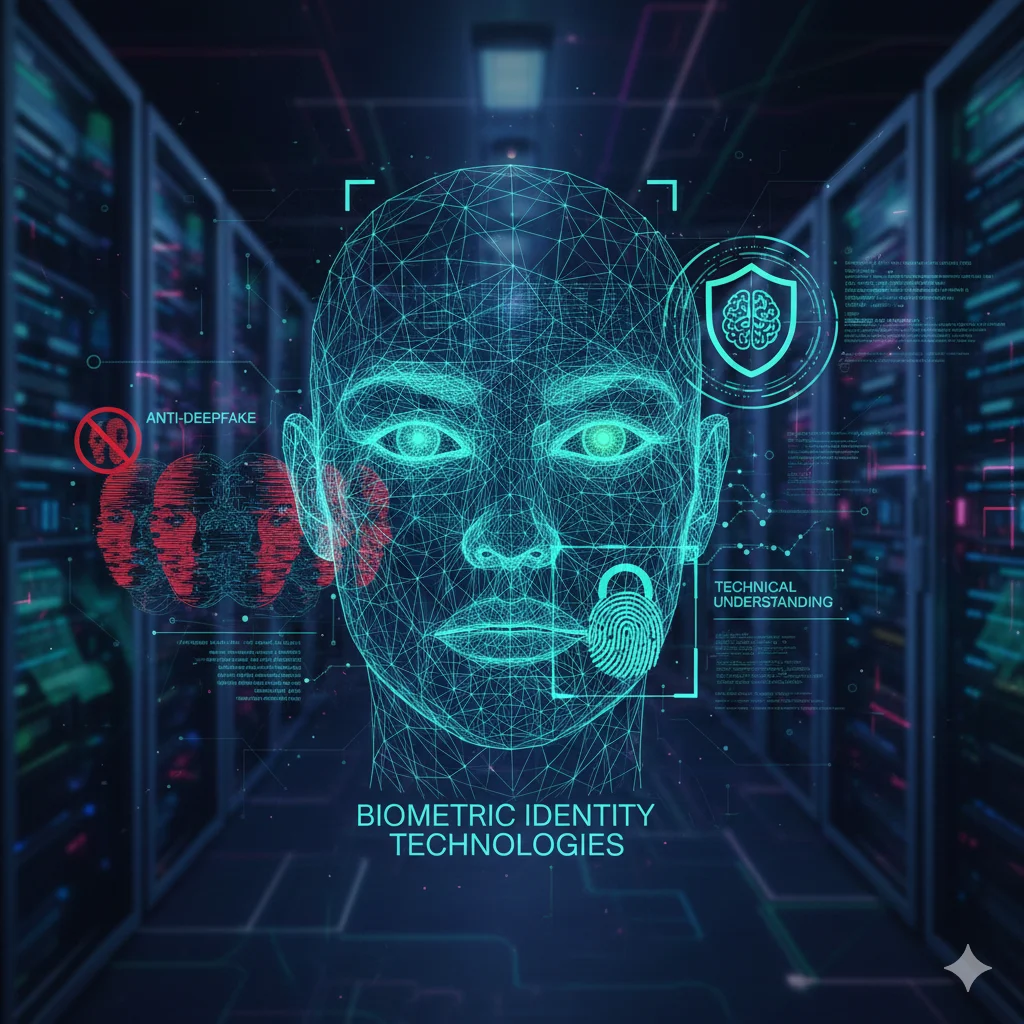
Whether you’re evaluating facial recognition for access control, implementing liveness detection for KYC, or defending against deepfakes in video verification, effective deployment begins with deep technical understanding.
Explore our technology-specific knowledge bases and discover what works in your context.