Introduction:
Synthetic identity fraud involves the creation of false identities for fraudulent purposes by combining real and fake information. Synthetic identity fraud is the process of creating entirely new identities by fusing authentic information, like a valid Social Security number (SSN), name, or date of birth, with fraudulent information, like addresses or phone numbers. This approach is in contrast to traditional identity theft, which entails stealing someone’s personal information. Unbeknownst to the people whose data is being stolen, these false identities are then used to create bank accounts, seek, or collect credit card debt.
Because it can remain undetected for a long period, this type of fraud is highly damaging. By the time the damage is done, typically in the form of a ruined credit score or a history of fraudulent financial activities, victims are sometimes unaware that their information has been compromised. To avoid falling victim to this growing financial crime, individuals and organizations must be aware of the key techniques used by criminals to create synthetic identities and be able to spot warning signs early. This article will review the specific methods used in synthetic identity fraud and explore ways to detect and prevent it.
Synthetic Identity:
The term “synthetic identity” describes a fake identity created by fusing various real and fake information, making it difficult to distinguish between the digital and physical traits that define a person. In the end, synthetic identities are employed for evil purposes like illicit financial gain. Synthetic identity fraud is the creation of an entirely new identity that is unconnected to any actual person, in contrast to typical identity theft, which includes taking someone’s preexisting personal information. The goal of this fake identity is to make it seem real so that thieves may create false bank accounts, obtain credit without authorization, and carry out other illegal actions.
Synthetic Identity Fraud:
Establishing a false identity using actual people’s personal information to obtain digital services and products is known as synthetic identity fraud. For example, fraudsters can combine the authentic information of many random individuals to create a new persona. Additionally, they can employ AI-generated demographics in addition to a single authentic component. Fraudsters sometimes provide personal phone numbers and email addresses to take control of the account and take money out.
Synthetic identities come in a wide variety. The main idea is that these artificial personas are products of malevolent imagination rather than actual people
How Synthetic Identity Fraud Works:
Making a fake identity seem genuine, trustworthy, and able to pass verification procedures and receive communications is the intricate process of synthetic identity fraud. It’s a long-term scam that can cause financial institutions and the people whose identity was compromised to suffer big losses while offering threat actors large payments. Although this identity isn’t associated with a specific individual, it appears authentic enough to deceive organizations such as banks, lenders, or governmental organizations. These fake identities allow the fraudster to open accounts, obtain loans, or carry out criminal activities without being discovered right away. This is how it usually operates:
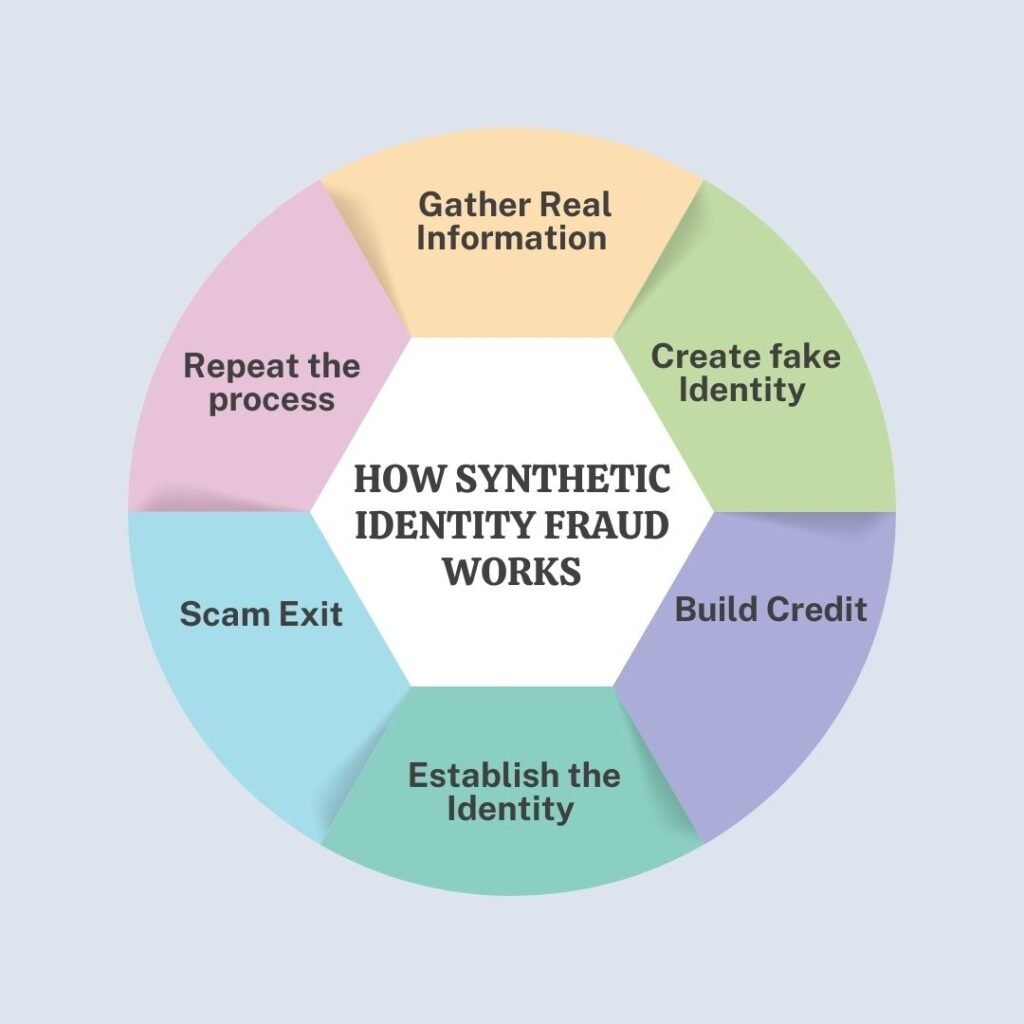
- Gather Real Information
- Create fake Identity
- Build Credit
- Establish the Identity
- Scam Exit
- Repeat the process
Gather Real Information:
The criminal of the fraud will frequently make use of real pieces of personal information, such as an actual Social Security number (SSN) that relates to a person (typically a child, someone with a small credit history, or a person who hasn’t been using their SSN very much), in conjunction with other details that have been fabricated, such as a fake name, date of birth, and place of residence. Common sources included.
- Data Leaks
- Security breaches
- Data Exposure
- Cybersecurity breaches
- Information breaches
Create Fake Identity:
Fraudsters frequently combine a stolen Social Security number with fabricated information, such as a fictitious name, phone number, date of birth, or address. This is a typical practice. It is this combination of actual and fabricated data that constitutes a synthetic identity. This combination is sometimes referred to as “Creature ID.”
Build Credit:
Scammers use the synthetic ID to apply for lines of credit with the intent of eventual theft. At first, applications frequently face rejection and dismissal because of insufficient credit history. Nonetheless, these applications generate a financial record for the synthetic identity.
Fraud patients persist in seeking credit until they achieve success, frequently turning to high-risk lenders. By committing to their synthetic identity over the long term, they manage this credit wisely, ensuring timely payments to establish a strong credit history and enhance their overall credibility.
Establish the Identity:
Once the fraudulent individual has established their credit score, they are able to raise their credit limits, obtain loans, or make significant expenditures. Since the identity looks real, these fraudulent actions may go undetected.
Scam Exit:
The scam artist makes one last attempt to max out all available credit before disappearing and ignoring any payback once the fake identity has successfully built up authentic credit and is able to borrow money from financial institutions. This procedure is commonly known as “exposing off,” and it results in large losses for creditors. It might be challenging to track down the offender or retrieve losses if they decide to give up the fake identity and create a new one.
Techniques to Detect Synthetic Identity Fraud:
Although it might be difficult to identify synthetic identity fraud, there are certain important indicators to watch out for and actions to take. Here are a few easy methods to identify it:
Strange Credit Activity:
In the context of credit, “strange credit activity” refers to abrupt and surprising changes in credit scores as well as quick fluctuations. Moreover, it may entail a credit history that is extremely brief or superficial, which is a characteristic that is frequently associated with synthetic identities. Such behavior is frequently an indication that someone is constructing a phony credit profile in a snap.
Mismatched information:
When the details given don’t match official records such as names, residences, or dates of birth, this is known as mismatched information. Additionally, it may display discrepancies across several databases or applications. Such information is a warning sign that can point to a fake identity.
Odd behavior:
Applying for several credit accounts quickly is an example of odd conduct, which is frequently observed when people use fictitious identities to try to create a false credit history. Additionally, it entails abrupt high-value transactions following a lull in credit activity. These trends may indicate dishonest activity.
Regular account reviews:
Reviewing accounts on a regular basis entails looking for odd activity, particularly in accounts with little or no credit history. This process makes it easier to spot any irregularities or questionable modifications early on. Monitoring authorized user accounts is crucial for detecting any fraudulent activity.
Strong verification process:
Adding additional security layers, such as multifactor authentication or biometric checks, to verify identification is part of a robust verification process. You may confirm that the individual is who they say they are by asking knowledge-based questions. Precautions reduce the likelihood of synthetic identity fraud.
Preventions for Synthetic Identity Fraud:
A mixture of awareness-raising, technology advancements, and proactive measures is needed to prevent synthetic identity theft. Preventing this kind of fraud necessitates a multi-layered strategy to defend against fraudulent behavior since it is difficult to identify and frequently combines fake and authentic information. To lower the danger of synthetic identity fraud, people, companies, and financial institutions should implement the following strategies:
- Biometric identification
- SSN and Address verification
- Credit application review
- Behavioural analysis
- Fraud alerts and freeze
- Alerts for institutions
- KYC Regulations
- Limiting data access
Biometric identification:
An additional degree of protection is provided by using biometric technology such as voice recognition, fingerprints, and face recognition. The approach makes it more difficult for fraudulent activities to employ synthetic identities, which may contain authentic data but fabricated or modified details.
SSN and Address verification:
To make sure that the information supplied is accurate and in line with public records, financial institutions should make use of data verification systems that verify names, addresses, and Social Security numbers with databases maintained by the government and other official sources.
Behavioral analysis:
Banks and other financial organizations can identify departures from normal activity by monitoring and evaluating user behavior. For instance, when a synthetic identity begins making abnormally large purchases or seeking credit lines, it may raise an alarm for further inquiry.
Alerts for Institutes:
Customers should receive real-time warnings from financial institutions whenever there are notable changes to their credit reports or accounts. Such notifications can aid in the early detection of possible fraud, particularly when a false identity is utilized to make purchases or create a new credit line.
KYC Regulations:
Implementing good KYC standards guarantees that companies check the identification of their consumers before participating in financial transactions. Financial organizations must comply with regulatory norms that prohibit synthetic identities from being established or used without sufficient verification.
Conclusion:
Synthetic identity fraud is a severe problem that is on the rise and has the potential to lead victims to face significant financial difficulties. Usually it is not detected until a large amount of harm has already been dealt with. Both people and corporations can take measures to protect themselves by being aware of the warning indications and employing improved detection procedures. When it comes to preventing the long con of fraud, early identification and prevention are essential components.





